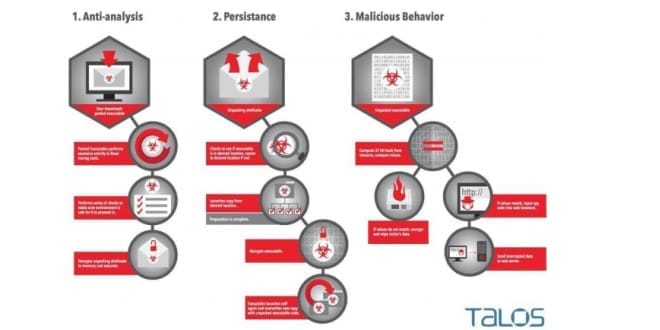
Cisco system’s anti-virus swat team, Telos, has issued a warning about a new malware threat that takes a scorched earth policy to its key logging activities. The malware has been codenamed Rombertik. Like most modern types of malware, Rombertik has several screens that it uses to evade detection. In attempting to reverse engineer the malware through a ‘sandbox approach,’ wherein the malware was activated in a quarantined and instrumented environment, the Telos team discovered that the virus wrote a random byte of data over 960 million times, thereby stalling it’s execution while confounding the detector by not actually hibernating, like regular malware. This was but one of the innovative evasive techniques discovered before the researchers triggered its ‘nuclear option.’ Beyond the junk code technique, researchers discovered an unpacking code so sophisticated and complex that they describe it both as ‘monstrous’ and ‘nightmarish.’
In the process of reverse engineering Rombertik, Talos discovered multiple layers of obfuscation and anti-analysis functionality. This functionality was designed to evade both static and dynamic analysis tools, make debugging difficult. If the sample detected it was being analyzed or debugged it would ultimately destroy the master boot record (MBR).At the moment the malicious software seems to be distributed through an email attachment that masquerades as a .pdf but is actually a .scr. As explained by Daily Tech, screensaver files are becoming “increasingly popular exploit vector(s)… as they are allowed to execute shell script code.”
The warning comes after a year where ransomware, another particularly vicious kind of malware, was thrust into the public consciousness. Whereas Rombertik is simply looking to steal passwords and credit card info, ransomware or cryptolocking viruses demand a direct payment from the victim in order to regain access to their files. Pc world has an excellent guide to identifying and dealing with various kinds of ransomware viruses.
Stay safe folks, and for the love of God, don’t open that e-mail attachment if you don’t know what it is!