Security firm Check Point Software Technologies has found malware that has breached more than One Million Google Accounts. They’ve named this malware campaign “Gooligan”, and claim it is breaching a further 13,000 devices every day. Gooligan is a new variant of malware known as “Ghost Push”.
The exploit works through infected apps installed via the Google Play Store. Once installed, the app roots the device, installs further software, and records the email account, login information, then installs adware. It uses two known flaws, known as VROOT and Towelroot to gain root access.
After achieving root access, Gooligan downloads a new, malicious module from the C&C server and installs it on the infected device. This module injects code into running Google Play or GMS (Google Mobile Services) to mimic user behavior so Gooligan can avoid detection, a technique first seen with the mobile malware HummingBad. The module allows Gooligan to:- Steal a user’s Google email account and authentication token information - Install apps from Google Play and rate them to raise their reputation - Install adware to generate revenue
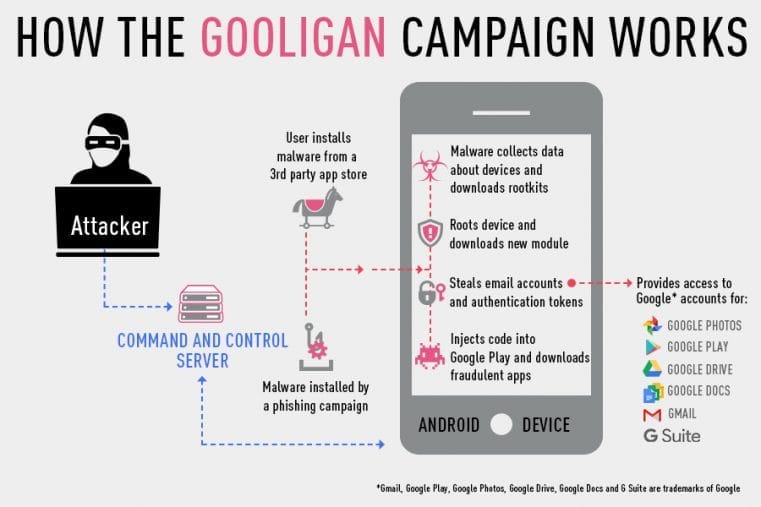
These vulnerabilities affect all devices running Android 4.x (Ice Cream Sandwich) through 5.x (Lollipop). With current Android usage share, this accounts for 74.3% of all active Android devices. Because it directly steals the authentication token, two-factor authentication does not protect against Gooligan. If infected, Checkpoint recommends a complete wipe of the device and an immediate password change.
Adrian Ludwig, Google’s Director of Android Security, has published a statement on Google+ regarding Gooligan. While it can steal personal information, Ludwig says there is “no evidence” of it directly accessing user data, noting “The motivation behind Ghost Push is to promote apps, not steal information, and that held true for this variant.” Ludwig also said that affected users that have been found have had their authentication tokens revoked, with instructions on how to proceed.
Checkpoint’s announcement contains a list of known infected apps. They have also set up a page to check if an account has been compromised. While it is not protection against Gooligan, enabling two-factor authentication is also recommended as a general security practice.







